Привет! Сегодня мы расскажем про то как настроить Site-To-Site IPSec VPN туннель между роутерами Cisco. Такие VPN туннели используются обеспечения безопасной передачи данных, голоса и видео между двумя площадками (например, офисами или филиалами). Туннель VPN создается через общедоступную сеть интернет и шифруется с использованием ряда продвинутых алгоритмов шифрования, чтобы обеспечить конфиденциальность данных, передаваемых между двумя площадками.

Настройка Site-To-Site IPSec VPN на Cisco

В этой статье будет показано, как настроить и настроить два маршрутизатора Cisco для создания постоянного безопасного туннеля VPN типа «сеть-сеть» через Интернет с использованием протокола IP Security (IPSec) . В рамках статьи мы предполагаем, что оба маршрутизатора Cisco имеют статический публичный IP-адрес.
ISAKMP (Internet Security Association and and Key Management Protocol) и IPSec необходимы для построения и шифрования VPN-туннеля. ISAKMP, также называемый IKE (Internet Key Exchange) , является протоколом согласования (negotiation protocol), который позволяет двум хостам договариваться о том, как создать сопоставление безопасности IPsec. Согласование ISAKMP состоит из двух этапов: фаза 1 и фаза 2.
Во время фазы 1 создается первый туннель, который защищает последующие сообщения согласования ISAKMP. Во время фазы 2 создается туннель, который защищает данные. Затем в игру вступает IPSec для шифрования данных с использованием алгоритмов шифрования и предоставляющий аутентификацию, шифрование и защиту от повторного воспроизведения.
Требования к IPSec VPN
Чтобы упростить понимание настройки разделим его на две части:
- Настройка ISAKMP (Фаза 1 ISAKMP)
- Настройка IPSec (Фаза 2 ISAKMP, ACL, Crypto MAP)
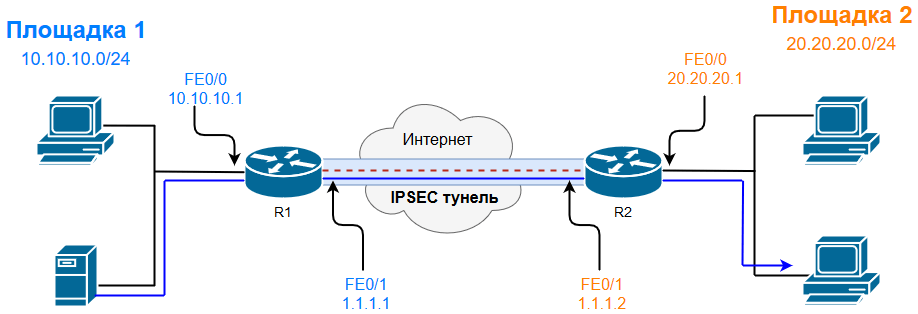
Делать будем на примере, который показан на схеме – два филиала, оба маршрутизатора филиалов подключаются к Интернету и имеют статический IP-адрес, назначенный их провайдером. Площадка №1 имеет внутреннею подсеть 10.10.10.0/24, а площадка №2 имеет подсеть 20.20.20.0/24. Цель состоит в том, чтобы безопасно соединить обе сети LAN и обеспечить полную связь между ними без каких-либо ограничений.
Настройка ISAKMP (IKE) - ISAKMP Phase 1
IKE нужен только для установления SA (Security Association) для IPsec. Прежде чем он сможет это сделать, IKE должен согласовать отношение SA (ISAKMP SA) с одноранговым узлом (peer).
Начнем с настройки маршрутизатора R1 первой площадки. Первым шагом является настройка политики ISAKMP Phase 1:
R1(config)# crypto isakmp policy 1 R1(config-isakmp)# encr 3des R1(config-isakmp)# hash md5 R1(config-isakmp)# authentication pre-share R1(config-isakmp)# group 2 R1(config-isakmp)# lifetime 86400
Приведенные выше команды означают следующее:
- 3DES - метод шифрования, который будет использоваться на этапе 1
- MD5 - алгоритм хеширования
- Pre-Share - использование предварительного общего ключа (PSK) в качестве метода проверки подлинности
- Group 2 - группа Диффи-Хеллмана, которая будет использоваться
- 86400 - время жизни ключа сеанса. Выражается либо в килобайтах (сколько трафика должно пройти до смены ключа), либо в секундах. Значение установлено по умолчанию.
Мы должны отметить, что политика ISAKMP Phase 1 определяется глобально. Это означает, что если у нас есть пять разных удаленных площадок и настроено пять разных политик ISAKMP Phase 1 (по одной для каждого удаленного маршрутизатора), то, когда наш маршрутизатор пытается согласовать VPN-туннель с каждой площадкой, он отправит все пять политик и будет использовать первое совпадение, которое принято обоими сторонами.
Далее мы собираемся определить Pre-Shared ключ для аутентификации с нашим партнером (маршрутизатором R2) с помощью следующей команды:
R1(config)# crypto isakmp key merionet address 1.1.1.2
Pre-Shared ключ партнера установлен на merionet, а его публичный IP-адрес - 1.1.1.2. Каждый раз, когда R1 пытается установить VPN-туннель с R2 (1.1.1.2), будет использоваться этот ключ.
Настройка IPSec – 4 простых шага
Для настройки IPSec нам нужно сделать следующее:
- Создать расширенный ACL
- Создать IPSec Transform
- Создать криптографическую карту (Crypto Map)
- Применить криптографическую карту к общедоступному (public) интерфейсу
Давайте рассмотрим каждый из вышеперечисленных шагов.
Шаг 1: Создаем расширенный ACL
Нам нужно создать расширенный access-list (про настройку Extended ACL можно прочесть в этой статье) и в нем определить какой траффик мы хотим пропускать через VPN-туннель. В этом примере это будет трафик из одной сети в другую с 10.10.10.0/24 по 20.20.20.0/24. Иногда такие списки называют crypto access-list или interesting traffic access-list.
R1(config)# ip access-list extended VPN-TRAFFIC R1(config-ext-nacl)# permit ip 10.10.10.0 0.0.0.255 20.20.20.0 0.0.0.255
Шаг 2: Создаем IPSec Transform
Следующим шагом является создание набора преобразования (Transform Set), используемого для защиты наших данных. Мы назвали его TS.
R1(config)# crypto ipsec transform-set TS esp-3des esp-md5-hmac
Приведенная выше команда определяет следующее:
- ESP-3DES - метод шифрования
- MD5 - алгоритм хеширования
Шаг 3: Создаем Crypto Map
Crypto Map является последнем этапом нашей настройки и объединяет ранее заданные конфигурации ISAKMP и IPSec:
R1(config)# crypto map CMAP 10 ipsec-isakmp R1(config-crypto-map)# set peer 1.1.1.2 R1(config-crypto-map)# set transform-set TS R1(config-crypto-map)# match address VPN-TRAFFIC
Мы назвали нашу криптографическую карту CMAP. Тег ipsec-isakmp сообщает маршрутизатору, что эта криптографическая карта является криптографической картой IPsec. Хотя в этой карте (1.1.1.2) объявлен только один пир, существует возможность иметь несколько пиров.
Шаг 4: Применяем криптографическую карту к общедоступному интерфейсу
Последний шаг - применить криптографическую карту к интерфейсу маршрутизатора, через который выходит траффик. Здесь исходящим интерфейсом является FastEthernet 0/1.
R1(config)# interface FastEthernet0/1 R1(config- if)# crypto map CMAP
Обратите внимание, что интерфейсу можно назначить только одну криптокарту.
Как только мы применим криптографическую карту к интерфейсу, мы получаем сообщение от маршрутизатора, подтверждающее, что isakmp включен: “ISAKMP is ON”.
На этом этапе мы завершили настройку IPSec VPN на маршрутизаторе Площадки 1.
Теперь перейдем к маршрутизатору Площадки 2 для завершения настройки VPN. Настройки для R2 идентичны, с отличиями лишь в IP-адресах пиров и ACL.
R2(config)# crypto isakmp policy 1 R2(config-isakmp)# encr 3des R2(config-isakmp)# hash md5 R2(config-isakmp)# authentication pre-share R2(config-isakmp)# group 2 R2(config-isakmp)# lifetime 86400 R2(config)# crypto isakmp key merionet address 1.1.1.1 R2(config)# ip access-list extended VPN-TRAFFIC R2(config-ext-nacl)# permit ip 20.20.20.0 0.0.0.255 10.10.10.0 0.0.0.255 R2(config)# crypto ipsec transform-set TS esp-3des esp-md5-hmac R2(config)# crypto map CMAP 10 ipsec-isakmp R2(config-crypto-map)# set peer 1.1.1.1 R2(config-crypto-map)# set transform-set TS R2(config-crypto-map)# match address VPN-TRAFFIC R2(config)# interface FastEthernet0/1 R2(config- if)# crypto map CMAP
Трансляция сетевых адресов (NAT) и VPN-туннели IPSec
В реальной схеме трансляция сетевых адресов (NAT), скорее всего, будет настроена для предоставления доступа в интернет внутренним хостам. При настройке VPN-туннеля типа «Site-To-Site» обязательно нужно указать маршрутизатору не выполнять NAT (deny NAT) для пакетов, предназначенных для удаленной сети VPN.
Это легко сделать, вставив оператор deny в начало списков доступа NAT, как показано ниже:
Для первого маршрутизатора:
R1(config)# ip nat inside source list 100 interface fastethernet0/1 overload R1(config)# access-list 100 deny ip 10.10.10.0 0.0.0.255 20.20.20.0 0.0.0.255 R1(config)# access-list 100 permit ip 10.10.10.0 0.0.0.255 any
Для второго маршрутизатора:
R2(config)# ip nat inside source list 100 interface fastethernet0/1 overload R2(config)# access-list 100 deny ip 20.20.20.0 0.0.0.255 10.10.10.0 0.0.0.255 R2(config)# access-list 100 permit ip 20.20.20.0 0.0.0.255 any
Инициализация и проверка VPN-туннеля IPSec
К этому моменту мы завершили нашу настройку, и VPN-туннель готов к запуску. Чтобы инициировать VPN-туннель, нам нужно заставить один пакет пройти через VPN, и этого можно достичь, отправив эхо-запрос от одного маршрутизатора к другому:
R1# ping 20.20.20.1 source fastethernet0/0 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 20.20.20.1, timeout is 2 seconds: Packet sent with a source address of 10.10.10.1 .!!!! Success rate is 80 percent (4/5), round-trip min/avg/max = 44/47/48 ms
Первое эхо-сообщение icmp (ping) получило тайм-аут, но остальные получили ответ, как и ожидалось. Время, необходимое для запуска VPN-туннеля, иногда превышает 2 секунды, что приводит к истечению времени ожидания первого пинга.
Чтобы проверить VPN-туннель, используйте команду show crypto session:
R1# show crypto session
Crypto session current status
Interface: FastEthernet0/1
Session status: UP-ACTIVE
Peer: 1.1.1.2 port 500
IKE SA: local 1.1.1.1/500 remote 1.1.1.2/500 Active
IPSEC FLOW: permit ip 10.10.10.0/255.255.255.0 20.20.20.0/255.255.255.0
Active SAs: 2, origin: crypto map
Готово! Мы только что успешно подняли Site-To-Site IPSEC VPN туннель между двумя маршрутизаторами Cisco!